Behind the Scenes at Not.email
2023-10-02

At Not.email, our core values revolve around privacy and security. We're thrilled to share the details of Not.email. While Not.email is available for free, premium features are also available to enhance the overall experience. Dive into the inner workings of Not.email with us and discover the stringent measures we've incorporated to guarantee your digital safety.
Article Outline
- Unpacking Burner Emails
- Tackling Domain Blacklisting
- Email Handling: Filtering, Sanitization, and Beyond
- Real-time Email Reception: The Wizardry Explained
- Amplifying Security with Two-Factor Authentication & More
- Infrastructure: Our Pillar of Reliability
- Tailoring Your Experience: Customizable Features
- The Power of End-to-End Encryption
- Conclusion
1. Unpacking Burner Emails
Burner emails act as a protective shield against spam. They're especially valuable when you need a temporary email—for instance, for a one-time sign-up. The best part? You won’t be left dealing with endless promotional emails afterward.
2. Tackling Domain Blacklisting
Like all temporary email services, we currently operate with a single domain. Over time, there's a risk of this getting blacklisted. We can always add more domains, but the challenge persists. The good news? Our custom domains offer a reliable backup plan.
3. Email Handling: Filtering, Sanitization, and Beyond
We take a straightforward approach to emails: you only receive emails if your inbox is actively open. If your inbox is closed or inactive, the email disappears. In essence, you control when you're available to receive emails by simply keeping your inbox open when you're expecting a message. To ensure safety, we have implemented several measures for your protection:
- DOMPurify for Sanitization: This helps cleanse incoming emails of potentially harmful content, ensuring that malicious scripts or code don't run when you view your emails.
- Strict Security Headers: By enforcing a rigid policy for security headers, we limit any potential interaction between your emails and unauthorized external servers. This means that trackers or other potential threats embedded in emails have less chance of compromising your privacy or security.
- DKIM and SPF validations: are email authentication methods designed to detect and prevent email spoofing. They ensure that the emails you receive are genuinely from the stated sender and haven't been tampered with. Although we accept and deliver all emails, those that don't pass these authentication checks will be flagged. This allows you to judge the credibility of the message for yourself.
With these safeguards, we aim to give you a clean and safe email experience while maximizing control over email credibility.
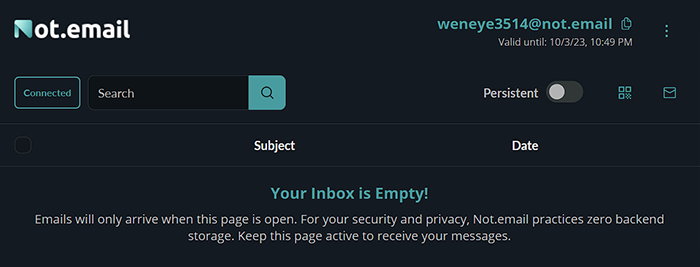
4. Real-time Email Reception
We've built a powerful infrastructure. Our setup includes multiple postfix agents, all guarded by a load balancer. When an email arrives, our backend decides if your inbox is active. If it is, you'll receive your email instantly via websockets. This setup keeps out spam, but you'll need to stay online to catch your emails.
Pros:
- Instant Delivery: You get emails the moment they are sent, ensuring real-time notifications without delays, which is crucial for time-sensitive tasks like account verifications or one-time codes.
- Enhanced Privacy: Since emails vanish if you're not online, there's no residual data stored. This transient nature ensures a higher level of data privacy.
- Spam Reduction: This method naturally filters out unsolicited emails. If you're not expecting an email, you're likely not online, and thus, random spam messages won't clog your inbox.
- Improved Security: Without a stored record of emails, there's a reduced risk of your temporary inbox being compromised and your data being exposed.
Cons:
- Need to Stay Active: To ensure you receive your email, you must keep your inbox open, which may not always be convenient.
- Potential for Missed Emails: If you close your inbox or get disconnected even for a brief period, there's a chance you could miss an email.
- Limited Utility for Prolonged Engagements: This approach is optimal for quick, one-off email interactions. For engagements requiring back-and-forth over an extended period, the need to remain active can be a hindrance.
For many users of temporary emails, the pros outweigh the cons. The system is designed for short-term tasks where the emphasis is on speed, privacy, and security, rather than prolonged engagement.
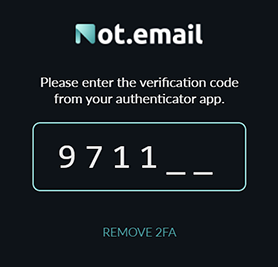
5. Amplifying Security with Two-Factor Authentication & More
Your security is our foremost priority. We've integrated multiple in-app measures to ensure your inbox remains your private domain:
- Secret Key for Every Inbox: Each inbox is protected by a unique secret key, accessible through a link or QR code.
- History-Bypassing Link: Worried about browser footprints? We've got you covered. The app allows you to paste and access the link directly, ensuring your actions leave no trace in your browser history.
- In-App QR Code Scanner: o enhance user convenience and security, our in-built QR code scanner lets you swiftly access your inbox without any external dependencies.
- Two-Factor Authentication (2FA): As an additional layer of fortification, we've implemented 2FA. Once activated, you'll require a code from your authenticator app to access your inbox, making sure it remains impenetrable to anyone but you.
Our commitment to security is holistic, integrating both inherent app features and supplementary layers like 2FA to provide you a safe and seamless experience.
6. Infrastructure: Our Pillar of Reliability
Our service stands tall on a robust digital architecture, meticulously designed for efficiency and scalability. Let’s delve into the four critical components:
Load Balancer
- Purpose: To evenly distribute incoming email traffic across multiple servers.
- Benefit: It ensures no single server is overwhelmed, guaranteeing quick email reception even during peak times.
Postfix Servers
- Purpose: These are dedicated mail transfer agents responsible for the initial reception of emails.
- Benefit: They conduct preliminary validations, such as DKIM and SPF checks. Regardless of validation results, emails are passed to the backend for further processing.
Backend
- Purpose: Acting as the central hub of our system, emails received by the postfix servers are immediately relayed to the backend server. Here, the system ascertains if an inbox is active. If it is, the email gets dispatched directly to the user. Otherwise, the email vanishes without a trace.
- Benefit: It enables real-time email delivery through websockets, ensuring you receive emails the moment they're sent, provided your inbox is online.
- Purpose: This robust database system manages all application data. Importantly, it does not store any information related to received emails.
- Benefit: Known for its scalability and resilience, it guarantees consistent performance, even as our user base grows.
Our commitment to top-notch infrastructure not only promises a smooth user experience but also ensures we're equipped to meet future demands seamlessly.
7. Tailoring Your Experience: Customizable Features
At Not.email, we merge customization with unparalleled security. Our standout offering is the ability to use distinguished custom domains in the realm of temporary emails. This feature not only adds a touch of professionalism but distinguishes your temporary email identity in a saturated market.
However, it isn’t just about domains. Even in our free version, we provide a versatile array of alias options. Whether it's straightforward word-number combinations or intricate random strings, there's an alias to cater to every user's preference. These complex aliases aren't merely for uniqueness. Their complexity makes them harder to guess, adding an additional security layer. The random generation feature ensures your chosen alias is distinct, considerably minimizing the risk of duplication.
In essence, with Not.email, you're guaranteed a tailored, secure, and efficient email experience.
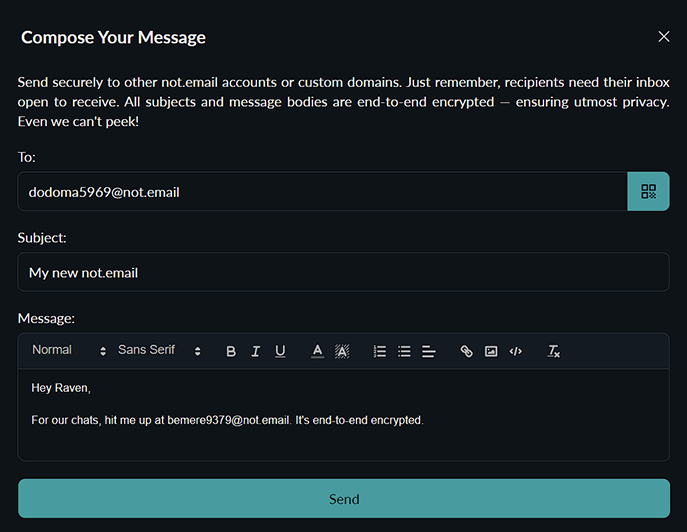
8. The Power of End-to-End Encryption
Our commitment to end-to-end encryption is unwavering, but it's essential to understand its scope. Only internal emails—that is, emails exchanged within the Not.email system—benefit from this highest level of encryption. Why? Because external emails, those sent from outside our secure environment, originate from servers and systems beyond our control. It's simply not feasible to guarantee end-to-end encryption for content that doesn't originate within our secure network.
However, once these emails enter our domain, we ensure that they're protected and handled with utmost security. And as for internal correspondences, they're fortified with the best encryption available. Even in the unlikely event of a backend breach, these internal emails would remain inaccessible, all thanks to our rigorous encryption and unwavering monitoring mechanisms. Our aim is clear and transparent: we are devoted to ensuring your internal communications are as private and protected as possible.
9. Conclusion
Ensuring your security and privacy is our mission. Explore Not.email and experience the next-gen email safety. If you spot areas for enhancement or have concerns, we're always here to listen.
